Receive notifications about channel events
A webhook is a user-defined callback over HTTPS that allows your app or back-end system to receive notifications when certain events occur. Agora calls your webhook endpoint from its servers to send notifications about Interactive Live Streaming events. With Notifications, you can subscribe to Interactive Live Streaming events and receive notifications in real time.
Understand the tech
Using Agora Console you subscribe to specific events for your project and configure the URL of the webhooks to receive these events. Agora sends notifications of your events to your webhook every time they occur. Your server authenticates the notification and returns 200 Ok to confirm reception. You use the information in the JSON payload of each notification to give the best user experience to your users.
The following figure illustrates the workflow when Notifications is enabled for the specific Interactive Live Streaming events you subscribe to:
Channel events notification workflow
- A user commits an action that creates an event.
- Notifications sends an HTTPS POST request to your webhook.
- Your server validates the request signature, then sends a response to Notifications within 10 seconds. The response body must be in JSON.
If Notifications receives 200 OK within 10 seconds of sending the initial notification, the callback is considered successful. If these conditions are not met, Notifications immediately resends the notification. The interval between notification attempts gradually increases. Notifications stops sending notifications after three retries.
Prerequisites
To set up and use Notifications, you must have:
-
A computer with Internet access.
If your network access is restricted by a firewall, call the IP address query API to retrieve the Notifications IP addresses , then configure the firewall to allow these IP addresses.
Handle notifications for specific events
In order to handle notifications for the events you subscribe to, you need to:
Create your webhook
Once Notifications is enabled, Agora SDRTN® sends notification callbacks as HTTPS POST requests to your webhook when events that you are subscribed to occur. The data format of the requests is JSON, the character encoding is UTF-8, and the signature algorithm is HMAC/SHA1 or HMAC/SHA256.
For Notifications, a webhook is an endpoint on an HTTPS server that handles these requests. In a production environment you write this in your web infrastructure, for development purposes best practice is to create a simple local server and use a service such as ngrok to supply a public URL that you register with Agora SDRTN® when you enable Notifications.
To do this, take the following steps:
-
Set up Go
Ensure you have Go installed on your system. If not, download and install it from the official Go website.
-
Create a Go project for your server
Create a new directory for your project and navigate into it:
In the project directory, create a new file
main.go. Open the file in your preferred text editor and add the following code: -
Run your Go server
Run the server using the following command:
-
Create a public URL for your server
In this example you use
ngrokto create a public URL for your server.-
Download and install ngrok. If you have
Chocolatey, use the following command: -
Add an
authtokento ngrok:To obtain an
authToken, sign up with ngrok. -
Start a tunnel to your local server using the following command:
You see a Forwarding URL and a Web Interface URL in the console. Open the web interface URL in your browser.
-
-
Test the server
Open a web browser and navigate to the public URL provided by
ngrokto see the root handler response.Use curl, Postman, or another tool to send a
POSTrequest tohttps://<ngrok_url>/ncsNotifywith the requiredJSONpayload.Example using
curl:Make sure you replace
ngrok_urlwith the forwarding url.Once the HTTP request is successful, you see the following
JSONpayload in your browser:
Enable Notifications
To enable Notifications:
-
Log in to Agora Console. On the Projects tab, locate the project for which you want to enable Notifications and click Edit.
-
In the All Features section, open the Notifications tab and click on the service for which you want to enable notifications. The section expands to show configuration options.
-
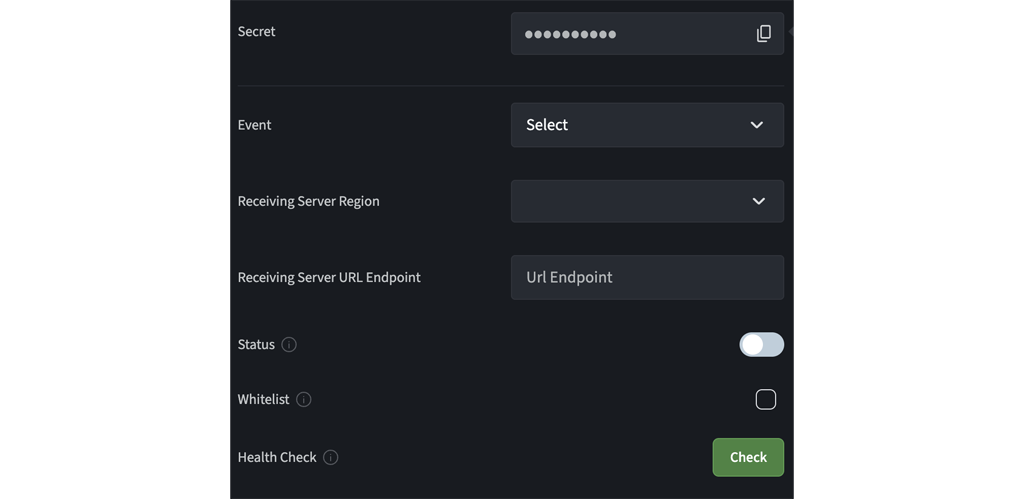
Fill in the following information:
-
Event: Select all the events that you want to subscribe to.
If the selected events generate a high number of queries per second (QPS), ensure that your server has sufficient processing capacity.
-
Receiving Server Region: Select the region where your server that receives the notifications is located. Agora connects to the nearest Agora node server based on your selection.
-
Receiving Server URL Endpoint: The
HTTPSpublic address of your server that receives the notifications. For example,https://1111-123-456-789-99.ap.ngrok.io/ncsNotify.infoFor enhanced security, Notifications no longer supports
HTTPaddresses.-
To reduce the delay in notification delivery, best practice is to activate
HTTPpersistent connection (also calledHTTPkeep-alive) on your server with the following settings:MaxKeepAliveRequests: 100 or moreKeepAliveTimeout: 10 seconds or more
-
-
Whitelist: If your server is behind a firewall, check the box here, and ensure that you call the IP address query API to get the IP addresses of the Agora Notifications server and add them to the firewall's allowed IP list.
-
-
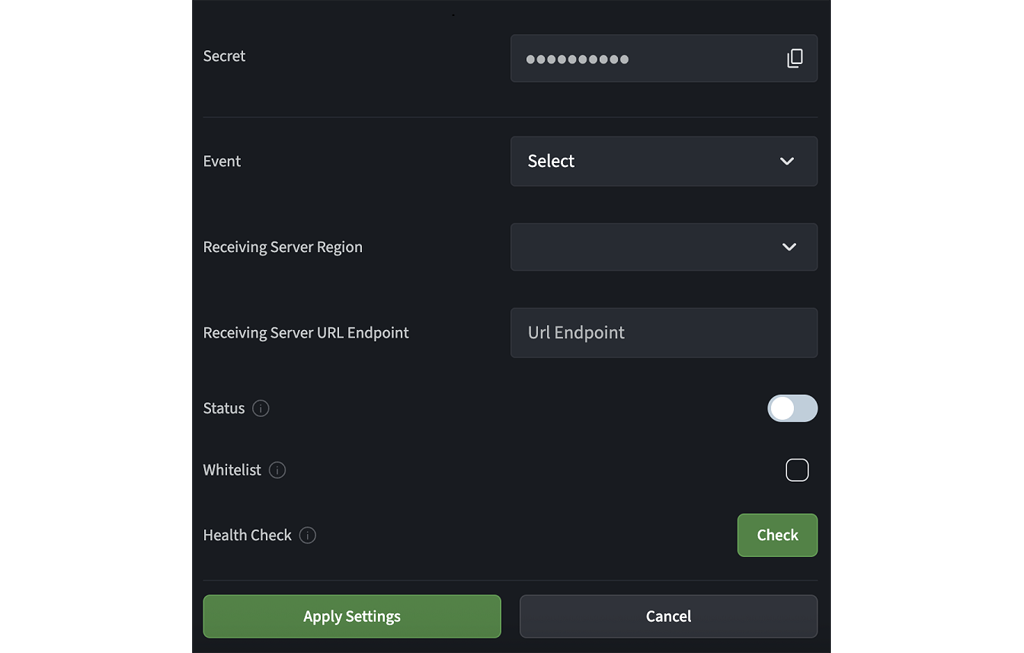
Copy the Secret displayed against the product name by clicking the copy icon. You use this secret to Add signature verification.
-
Press Check. Agora performs a health test for your configuration as follows:
-
The Notifications health test generates test events that correspond to your subscribed events, and then sends test event callbacks to your server.
In test event callbacks, the channelName is
test_webhook, and the uid is12121212. -
After receiving each test event callback, your server must respond within 10 seconds with a status code of
200. The response body must be in JSON format. -
When the Notifications health test succeeds, read the prompt and press Apply Settings. After your configuration is saved, the Status of Notifications shows Enabled.
If the Notifications health test fails, follow the prompt on the Agora Console to troubleshoot the error. Common errors include the following:
-
Request timeout (590): Your server does not return the status code
200within 10 seconds. Check whether your server responds to the request properly. If your server responds to the request properly, contact Agora Technical Support to check if the network connection between the Agora Notifications server and your server is working. -
Domain name unreachable (591): The domain name is invalid and cannot be resolved to the target IP address. Check whether your server is properly deployed.
-
Certificate error (592): The Agora Notifications server fails to verify the SSL certificates returned by your server. Check if the SSL certificates of your server are valid. If your server is behind a firewall, check whether you have added all IP addresses of the Agora Notifications server to the firewall's allowed IP list.
-
Other response errors: Your server returns a response with a status code other than
200. See the prompt on the Agora Console for the specific status code and error messages.
-
-
Video walkthrough
Add signature verification
To communicate securely between Notifications and your webhook, Agora SDRTN® uses signatures for identity verification as follows:
-
When you configure Notifications in Agora Console, Agora SDRTN® generates a secret you use for verification.
-
When sending a notification, Notifications generates two signature values from the secret using
HMAC/SHA1andHMAC/SHA256algorithms. These signatures are added asAgora-SignatureandAgora-Signature-V2to theHTTPSrequest header. -
When your server receives a callback, you can verify
Agora-SignatureorAgora-Signature-V2:- To verify
Agora-Signature, use the secret, the raw request body, and thecrypto/sha1algorithm. - To verify
Agora-Signature-V2, use the secret, the raw request body, and thecrypto/sha256algorithm.
- To verify
The following sample code uses crypto/sha1.
To add signature verification to your server, take the following steps:
-
In the
main.gofile, replace your imports with with the following: -
Add the following code after the list of imports:
-
In
main.go, add the following code after you read the request body: -
To test the server, follow the steps given in the Enable notifications section.
-
When you receive an event from the console, and if the signature matches, the event details are displayed in your browser.
Handle redundant notifications and abnormal user activity
When using Notifications to maintain the online status of your app users, your server might experience the following issues:
-
Message notifications are redundant. You receive multiple notifications because the Agora Notifications server can send more than one notification callback for each channel event to ensure reliability of the service.
-
Message notifications arrive out of order. Network issues cause callbacks to arrive at your server in a different order than the order of event occurrence.
To accurately maintain the online status of users, your server needs to be able to deal with redundant notifications and handle received notifications in the same order as events occur. The following section shows you how to use channel event callbacks to accomplish this.
Handle redundant or out of order notifications
Agora Notifications sends RTC channel event callbacks to your server. All channel events, except for 101 and 102 events, contain the clientSeq field (Unit64) in payload, which represents the sequence number of an event. This field is used to identify the order in which events occur on the app client. For notification callbacks reporting the activities of the same user, the value of the clientSeq field increases as events happen.
Refer to the following steps to use the clientSeq field to enable your server to handle redundant messages, and messages arriving out of order:
-
Enable Agora Notifications, and subscribe to RTC channel event callbacks. Best practice is to subscribe to the following event types according to your use-case:
- In the
LIVE_BROADCASTINGprofile:103,104,105,106,111, and112. - In the
COMMUNICATIONprofile:103,104,111, and112.
- In the
-
Use the channel event callbacks to get the latest status updates about the following at your server:
- Channel lists
- User lists in each channel
- Data for each user, including the user ID, user role, whether the user is in a channel, and
clientSeqof channel events
-
When receiving notification callbacks of a user, search for the user in the user lists. If there is no data for the user, create data specific to the user.
-
Compare the value in the
clientSeqfield of the latest notification callback you receive with that of the last notification callback handled by your server:- If the former is greater than the latter, the notification callback needs to be handled.
- If the former is less than the latter, the notification callback should be ignored.
-
When receiving notification callbacks reporting a user leaving a channel, wait for one minute before deleting the user data. If it is deleted immediately, your server cannot handle notifications in the same order as channel events happen when receiving redundant notifications or notifications out of order.
Deal with abnormal user activities
When your server receives a notification callback of event 104 with reason as 999, it means that the user is considered to have abnormal activities due to frequent login and logout actions. In this case, best practice is that your server calls the Banning user privileges API to remove the user from the current channel one minute after receiving such notification callback; otherwise, the notification callbacks your server receives about the user's events might be redundant or arrive out of order, which makes it hard for you to accurately maintain the online status of this user.
Implement online user status tracking
This section provides sample Go code to show how to use channel event callbacks to maintain online user status at your app server.
To maintain a user registry, take the following steps:
-
Replace the content of the
main.gofile with the following code: -
To test signature verification, follow the steps given in the Enable notifications section.
When adopting the solutions recommended by Agora to maintain user online status, you need to recognize the following:
-
The solutions only guarantee eventual consistency of user status.
-
To improve accuracy, notification callbacks specific to one channel must be handled in a single process.
Reference
This section contains in depth information about Notifications.
Request Header
The header of notification callbacks contains the following fields:
| Field name | Value |
|---|---|
Content-Type | application/json |
Agora-Signature | The signature generated by Agora using the Secret and the HMAC/SHA1 algorithm. You need to use the Secret and HMAC/SHA1 algorithm to verify the signature value. For details, see Signature verification. |
Agora-Signature-V2 | The signature generated by Agora using the Secret and the HMAC/SHA256 algorithm. You need to use the Secret and the HMAC/SHA256 algorithm to verify the signature value. For details, see Signature verification. |
Request Body
The request body of notification callbacks contains the following fields:
| Field name | Type | Description |
|---|---|---|
noticeId | String | The notification ID, identifying the notification callback when the event occurs. |
productId | Number | The product ID:
|
eventType | Number | The type of event being notified. For details, see event types. |
notifyMs | Number | The Unix timestamp (ms) when Notifications sends a callback to your server. This value is updated when Notifications resends the notification callback. |
payload | JSON Object | The content of the event being notified. The payload varies with event type. |
Example
Event types
The Agora Notifications server notifies your server of the following RTC channel event types when you use the RTC service:
| eventType | Event name | Description |
|---|---|---|
101 | channel create | Initializes the channel. |
102 | channel destroy | Destroys the channel. |
103 | broadcaster join channel | In the streaming profile, the host joins the channel. |
104 | broadcaster leave channel | In the streaming profile, the host leaves the channel. |
105 | audience join channel | In the streaming profile, an audience member joins the channel. |
106 | audience leave channel | In the streaming profile, an audience member leaves the channel. |
107 | user join channel with communication mode | In the communication profile, a user joins the channel. |
108 | user leave channel with communication mode | In the communication profile, a user leaves the channel. |
111 | client role change to broadcaster | In the communication profile in RTC v4. x products or in the streaming profile, an audience member switches their user role to host. |
112 | client role change to audience | In the communication profile in RTC v4. x products or in the streaming profile, a host switches their user role to audience member. |
101 channel create
This event type indicates that a channel is initialized (when the first user joins the channel). The payload contains the following fields:
| Field name | Type | Description |
|---|---|---|
channelName | String | The name of the channel. |
ts | Number | The Unix timestamp (s) when the event occurs on the Agora RTC server. |
Example
102 channel destroy
This event type indicates that the last user in the channel leaves the channel and the channel is destroyed. The payload contains the following fields:
| Field name | Type | Description |
|---|---|---|
channelName | String | The name of the channel. |
ts | Number | The Unix timestamp (s) when the event occurs on the Agora RTC server. |
lastUid | Number | The ID of the last user to leave the channel. info If multiple people leave the channel at the same time, Agora message notification may return different lastUids. You can choose any one of them. |
Example
103 broadcaster join channel
This event type indicates that a host joins the channel in the streaming profile. The payload contains the following fields:
| Field name | Type | Description |
|---|---|---|
channelName | String | The name of the channel. |
uid | Number | The user ID of the host in the channel. |
platform | Number | The platform type of the host's device:
|
clientType | Number | The type of services used by the host on Linux. Common return values include:
|
clientSeq | Number | The sequence number, which is used to identify the order in which events occur on the app client. You can use the value of this field to sort the events of a user into chronological order. |
ts | Number | The Unix timestamp (s) when the event occurs on the Agora RTC server. |
Example
104 broadcaster leave channel
This event type indicates that a host leaves the channel in the streaming profile. The payload contains the following fields:
| Field name | Type | Description |
|---|---|---|
channelName | String | The name of the channel. |
uid | Number | The user ID of the host in the channel. |
platform | Number | The platform type of the host's device:
|
clientType | Number | The type of services used by the host on Linux. Common return values include:
|
clientSeq | Number | The sequence number, which is used to identify the order in which events occur on the app client. You can use the value of this field to sort the events of a user into chronological order. |
reason | Number | The reason why the host leaves the channel:
|
ts | Number | The Unix timestamp (s) when the event occurs on the Agora RTC server. |
duration | Number | The length of time (s) that the host stays in the channel. |
Example
105 audience join channel
This event type indicates that an audience member joins the channel in the streaming profile The payload includes the following fields:
| Field name | Type | Description |
|---|---|---|
channelName | String | The name of the channel. |
uid | Number | The user ID of the audience member in the channel. |
platform | Number | The platform type of the audience member's device:
|
clientType | Number | The type of services used by the host on Linux. Common return values include:
|
clientSeq | Number | The sequence number, which is used to identify the order in which events occur on the app client. You can use the value of this field to sort the events of a user into chronological order. |
ts | Number | The Unix timestamp (s) when the event occurs on the Agora RTC server. |
Example
106 audience leave channel
This event type indicates that an audience member leaves the channel in the streaming profile. The payload includes the following fields:
| Field name | Type | Description |
|---|---|---|
channelName | String | The name of the channel. |
uid | Number | The user ID of the audience member in the channel. |
platform | Number | The platform type of the audience member's device:
|
clientType | Number | The type of services used by the audience member on Linux. Common return values include:
|
clientSeq | Number | The sequence number, which is used to identify the order in which events occur on the app client. You can use the value of this field to sort the events of a user into chronological order. |
reason | Number | The reason why the audience member leaves the channel:
|
ts | Number | The Unix timestamp (s) when the event occurs on the Agora RTC server. |
duration | Number | The length of time (s) that the audience member stays in the channel. |
Example
107 user join channel with communication mode
This event type indicates that a user joins the channel in the communication profile. The payload includes the following fields:
| Field name | Type | Description |
|---|---|---|
channelName | String | The name of the channel. |
uid | Number | The user ID of the user in the channel. |
platform | Number | The platform type of the host's device:
|
clientSeq | Number | The sequence number, which is used to identify the order in which events occur on the app client. You can use the value of this field to sort the events of a user into chronological order. |
ts | Number | The Unix timestamp (s) when the event occurs on the Agora RTC server. |
Example
108 user leave channel with communication mode
This event type indicates that a user leaves the channel in the communication profile. The payload includes the following fields:
| Field name | Type | Description |
|---|---|---|
channelName | String | The name of the channel. |
uid | Number | The user ID of the user in the channel. |
platform | Number | The platform type of the user's device:
|
clientSeq | Number | The sequence number, which is used to identify the order in which events occur on the app client. You can use the value of this field to sort the events of a user into chronological order. |
reason | Number | The reason why a user leaves the channel:
|
ts | Number | The Unix timestamp (s) when the event occurs on the Agora RTC server. |
duration | Number | The length of time (s) that the user stays in the channel. |
Example
111 client role change to broadcaster
This event type indicates that an audience member calls setClientRole to switch their user role to host in the streaming profile. The payload includes the following fields:
| Field name | Type | Description |
|---|---|---|
channelName | String | The name of the channel. |
uid | Number | The user ID of the user in the channel. |
clientSeq | Number | The sequence number, which is used to identify the order in which events occur on the app client. You can use the value of this field to sort the events of a user into chronological order. |
ts | Number | The Unix timestamp (s) when the event occurs on the Agora RTC server. |
Example
112 client role change to audience
This event type indicates that a host call setClientRole to switch their user role to audience member in the streaming profile. The payload contains the following fields:
| Field name | Type | Description |
|---|---|---|
channelName | String | The name of the channel. |
uid | Number | The user ID of the user in the channel. |
clientSeq | Number | The sequence number, which is used to identify the order in which events occur on the app client. You can use the value of this field to sort the events of a user into chronological order. |
ts | Number | The Unix timestamp (s) when the event occurs on the Agora RTC server. |
Example
IP address query API
If your server that receives notification callbacks is behind a firewall, call the IP address query API to retrieve the IP addresses of Notifications and configure your firewall to trust all these IP addresses.
Agora occasionally adjusts the Notifications IP addresses. Best practice is to call this endpoint at least every 24 hours and automatically update the firewall configuration.
Prototype
- Method:
GET - Endpoint:
https://api.agora.io/v2/ncs/ip
Request header
Authorization: You must generate a Base64-encoded credential with the Customer ID and Customer Secret provided by Agora, and then pass the credential to the Authorization field in the HTTP request header.
Request body
This API has no body parameters.
Response body
When the request succeeds, the response body looks like the following:
Each primary IP field shows an IP address of Notifications server. When you receive a response, you need to note the primary IP fields and add all these IP addresses to your firewall's allowed IP list.
Considerations
-
Notifications does not guarantee that notification callbacks arrive at your server in the same order as events occur. Implement a strategy to handle messages arriving out of order.
-
For improved reliability of Notifications, your server may receive more than one notification callback for a single event. Your server must be able to handle repeated messages.
TipTo implement a strategy to ensure that you log only one callback event and ignore duplicate events, use a combination of the
noticeIdandnotifyMsfields in the response body.
