Security
Information security policy
This section provides information security policy for Agora services.
Agora services provide built-in encryption and customized encryption. You can use either of them to implement encryption. The following diagram describes the encrypted data transmission process:
Encrypted data transmission process
Purpose
Agora is committed to safeguarding the confidentiality, integrity, and availability of all users' physical and electronic information assets.
- Confidentiality against unauthorized access and eavesdropping
- Integrity against tampering and forgery
- Availability of data transmission through the Agora SD-RTN™
Scope
This article describes how Agora protects customer data with security controls.
Data classification
All customer data, in all formats or media types, is classified according to the following categories and protected accordingly.
Data classification categories
| Category | Description |
|---|---|
| Customer Account Data | Information related to the customers' Agora accounts, including customer ID, customer IP, network type, operating system, email address, telephone, product interest, programing platform, UTM information, identity, company name, company URL, billing information, trade information, purchased package information, project status, ticket, member information and console access record. |
| End User Data | Information collected by customers related to end users' personal devices and network, including microphone and camera information, CPU status, memory status, battery status, system version, phone model, phone signal level, received signal strength indicator (RSSI), network type, user attributes and channel attributes. |
| Call Content | Audio and video data of the user during a call. |
| Log | Media server logs generated by the Agora servers when accessing the Agora SD-RTN™. |
Data security
The communication between the user and the Agora server is protected by transmission protocols, such as the Agora private transmission protocol, Transport Layer Security (TLS) and Web Socket Secure (WSS). You can also use Advanced Encryption Standard (AES) or a customized encryption algorithm for the encryption of audio and video data.
During data transmission, the Agora SD-RTN™ does not transmit any encryption key information. Call content information can only be decrypted on the terminal device (such as the client app and the customer's on-premise recording server) through the client authorization key.
Data availability
- Large and distributed data centers: Agora has multiple data centers providing services globally, and any attack on one data center cannot affect others.
- Rapid recovery: When a data center is subjected to malicious attacks that are difficult to prevent, such as a distributed denial-of-service (DDoS) attack, Agora will automatically isolate the data center and avoid affecting users' services.
- DDoS attack prevention: Agora has deployed anti-DDoS firewalls in each core cloud data center. Agora has more than two hundred distributed data centers around the world, which guarantees sufficient capabilities and resources to control the risk of DDoS attacks.
Data storage
Agora provides customers with the Agora On-Premise Recording SDK and Agora Cloud Recording, enabling customers to record part or all of the call contents. When using the recording services, all recorded video or audio files are stored on the storage server provided by the customer.
Access authorization
End users can access the Agora SD-RTN™ using a dynamic key, see Secure authentication with tokens.
Electronic access controls
Agora strictly controls the data access on all internal systems. All users have independent internal accounts and authorization systems, and must pass two-step verification. All access records are recorded.
All servers involving user data are strictly audited and protected. Agora employees will only access the production server when necessary, and only by obtaining temporary authorization. Operation records are kept for the whole process.
Physical access controls
All operating servers are hosted in computer rooms that meet ISO 27001 or above information security management certification standards, and all computer rooms protect information security in accordance with the escrow agreement or the Data Protection Association (DPA). Both third-party hosting providers and Agora employees must be approved before they can access servers and equipment.
Roles and responsibilities
Agora sets the responsibilities for its own staff and customers. See the following sections for more information.
Roles and responsibilities within Agora
Security roles and responsibilities within Agora are categorized as follows:
Agora roles and responsibility categories
| Role | Responsibilities |
|---|---|
| Information Security Sub-Committee | The Information Security Sub-committee (ISSC) is responsible for the development and implementation of policies and procedures. The ISSC monitors company adherence, and conducts regular technical and non-technical evaluations of Agora security policies. The ISSC also designates which employees are authorized employees. |
| Authorized Employee | An authorized employee has access to the production machines required for the support and maintenance of the Agora service as determined by the ISSC. |
| All Other Staffs | All other staff are required to maintain confidentiality as required by their terms of employment and are required to immediately report of any security breach. |
Shared responsibilities
When evaluating the Agora SD-RTN™, it is important for customers to understand and distinguish the following security measures:
- The security measures that Agora implements and operates.
- The security measures that customers implement and operate to ensure the security of call content information and application when using the Agora SD-RTN™ services.
Customers retain control of the security measures they choose to protect their personal information, platform, applications, systems, and networks. Agora customers should be responsible for all information they collect from users and themselves, such as application logins, identities, passwords, payment information, names, and addresses.
Agora recommends adding obvious prompts before accessing the users' personal information. For example, add an Enable/Disable button with which the user can agree or disagree to share personal information.
Security training
Agora conducts information protection, security and compliance training for all new employees. Agora also ensures that all employees receive information confidentiality training at least once a year. All authorized employees (employees who have access to the production machines) will receive additional training.
Non-compliance
Employees must comply with confidentiality agreements and internal security systems. If a non-compliant situation occurs, Agora will take the corresponding measures depending on the severity of the situation, including but not limited to having conversations with the at-fault employees, strengthening training and education, dissolving labor agreements, and pursuing other legal liabilities.
Reporting potential security risks
How to report
Please report any potential risks of Agora services that you may notice to security@agora.io. Please use our PGP public key (Key ID: 2F4553BE) to encrypt your report, as potential security risks are usually sensitive. We assure our security experts will handle the issue immediately once they receive your report.
To facilitate troubleshooting and verification, please include the following information in your email:
- Your contact information.
- The version of the impacted SDK or solution.
- Description of the potential risks.
- Miscellaneous technical details, such as your system configurations, methods or steps for reproducing the issue.
To better protect our system and customers, Agora also invites security researchers to report any bug or vulnerabilities they discover to us. Click Bug Bounty to know more.
Security FAQ
How do I use an Agora SDK to protect my data security?
To ensure the security of the transmitted data, Agora services provide the encryption for audio and video data. Customers can use AES-128/AES-256 or other algorithms preset by Agora, or use customized encryption algorithms to achieve encryption, see Channel Encryption. The encryption key is completely generated and distributed by the customer. Agora recommends that customers use separate keys for each channel to achieve the highest level of data security.
Is Agora AES encryption mode secure?
For network protocol encryption, Agora SDKs use AES_128 mode to encrypt network payload.
For channel encryption, Agora SDKs support AES_128/AES_256 mode to encrypt audio and video. For those who have higher requirements for content security, Agora recommends using our customized encryption. Note that the On-Premise Recording SDK and Cloud Recording does not support customized encryption. For details, please send email to support@agora.io.
Is Agora HIPAA compliant?
Yes.
How does the Agora network respond to DDoS attacks?
Agora regularly scans core network nodes to check and clear possible security holes. Agora also configures anti-DDoS firewalls in each core cloud data center to protect them from attacks. Agora has more than two hundred distributed data centers around the world, which guarantees sufficient capabilities and resources to control the risk of DDoS attacks.
Does the Agora server cache audio and video data?
When using Agora services, the audio and video data are transmitted through the Agora servers. Agora servers cache the audio and video data for 10 seconds during the transmission and release all audio and video data immediately after the call.
Whitepaper
People engage longer when they see, hear, and interact with each other. The future of meaningful human connections is made possible now with Agora’s Real-Time Engagement Platform. People rely on Agora’s Real-Time Engagement Platform to exchange millions of calls and messages, with vivid voice and video embedded in any application, on any device, anywhere.
Agora, Inc. is proud to offer the professional Real-Time Engagement Platform as a Service (RTE PaaS) with Compliance, Safety, Security, and Trust. Our commitment to compliance, data, and information security and privacy protection is a part of the core values of our company. From our Software Defined Real-Time Network (SD-RTN™) architecture to our day-to-day business operations, Agora continually invests in innovations and business processes that build trust with our customers, investors, and developer community. Agora works to high standards to follow the best security practices and comply with strict privacy regulations and standards as we respect the privacy of all our customers.
The information contained in this document is intended to provide transparency in relation to Agora’s security stance and processes. If you think you may have found a security vulnerability within any of Agora’s services, please contact our security team directly at security@agora.io.
Agora security programs
Agora thrives to incorporate security into all our products and services and integrates the best security practices into everyday business operations. To meet these primary goals and improve the overall information security posture in an efficient and effective manner, Agora has built its security framework against the ISO27001 Information Security Management Standard.
As threats to information security continue to evolve, having dedicated security resources is essential. Agora’s Executive Security Committee meets regularly to address security concerns and coordinate company-wide security initiatives. The Agora Strategic Security Program Roadmap has been developed and approved by the committee to guide the implementation of our security programs. Our dedicated security team, led by the Chief Information Security Officer, has the responsibility for building and enforcing information security programs.
Ongoing monitoring and improvement
Agora is always looking to better protect its systems and customers. Therefore, we continuously monitor and improve our Information Security Programs by implementing the following:
- Agora conducts an internal audit of its information security management system at least once a year to ensure effectiveness;
- Agora follows industry best practice software development lifecycle management processes and conducts internal security reviews and testing before deployment into production systems;
- Agora engages third-party security experts to carry out regular penetration tests;
- Through our Bug Bounty Program, Agora works with security researchers to keep our customers data more secure by identifying and reporting vulnerabilities in our products and services.
Security compliance
Agora adheres to regional and international information security standards as well as industry requirements and is committed to using international best practices. We engage with independent third parties to verify the compliance of Agora. Certified by various reputable agencies across the globe, we are recognized by industry and security organizations for excellence.
Compliance certifications and attestations
ISO/IEC 27001 Information Security Management Standard
Agora is certified to ISO/IEC 27001:2013 by DNV GL, demonstrating our information security maturity level. Our security team implements the Information Security Management System in partnership with Ernst & Young. Security is a top priority at Agora, and this achievement demonstrates our commitment and continuous efforts to improve the efficiency of information security controls.
Click to download the certificate: ISO/IEC 27001:2013
ISO/IEC 27018 Information Technology – Security techniques – Code of practice for protection of personally identifiable information (PII) in publics clouds acting as PII processors
Agora is certified to ISO/IEC 27018 by DNV GL. This standard is a Code of Practice for protecting personal data in the cloud environment. Agora continuously strives to protect the sensitive data with our customers.
Click to download the certificate: ISO/IEC 27018:2019
SOC 2 Report
Agora is confident with our security practices and we continue to engage independent third parties to perform a strict SOC 2 audit on our internal processes, security controls and the design of Agora products. We meet all audit requirements set by the American Institute of Certified Public Accounts (AICPA) standards for security, availability and confidently and achieves the SOC 2 report.
PCI DSS
Agora prioritizes the security and privacy of its customers. Since we are neither a merchant nor a service provider as defined by the PCI Security Standards Council, we do not need to conduct an annual PCI assessment. However, Agora ensures that all transactions and customer data are handled with the highest level of security, in alignment with industry best practices. Should you have any questions or require further information regarding our security measures, please feel free to contact us at security@agora.io.
Regional security and data privacy regulations
General Data Protection Regulation - GDPR Agora is aligned with GDPR and we are committed to providing GDPR compliant products and services to our customers in the EU region or with our customers who conduct business within the EU.
Health Insurance Portability and Accountability Act -HIPAA Agora is aware of the sensitivity of transmitting and processing health information and we have invested in both the creation and ongoing maintenance of a HIPAA compliance program.
California Consumer Privacy Act - CCPA The CCPA is the first comprehensive privacy law in the United States that aims to provide a variety of privacy rights to California consumers. As a service provider, Agora is aligned with CCPA though the implementation of our security programs.
Children’s Online Privacy Protection Act - COPPA The COPPA regulates the privacy protection requirements for children under the age of thirteen. Agora has engaged privacy experts in meeting the requirements of COPPA.
Product security
Agora strongly believes in the principles of Secure by Design and Defense in Depth. Therefore, Agora adopts industry recognized security standards and best security practice at every layer - from infrastructure to application, in order to perfect our products and environment, and to secure the organization and our customers.
Identity and access management
Securing access to your environment starts with identity and access controls. Agora provides you with a solution to ensure that only authorized people can access your services and resources. The Agora Console is a role-based access control tool that you utilize to restrict access based on "the-need-to-know" principle. The console is an interactive interface where you can easily create accounts, revoke members and assign roles and permissions. This tool can assist you to enforce your security policies.
Furthermore, Agora provides static key, dynamic key, and hybrid authentication methods to secure the communication channels in different use-cases.
Data protection and encryption
At Agora, you choose how your content is secured. We offer you various options for your content in transit and provide you with full control of your own encryption keys. There features include:
- Agora Software Development Kits (SDKs) provide built-in encryption algorithm including AES-128 and AES-256 to protect all data transmitted between the end users and Agora services.
- We also provide you with the choice to use your own encryption algorithm to protect users’ media stream during real-time engagement. The encryption key is completely under your control.
- The communication between the end users and Agora network (that is, SD-RTN™) is protected by encrypted transmission protocols such as the Agora Private Transmission Protocol, Transport Layer Security (TLS) and WebSocket Secure (WSS).
Data storage
Agora offers our customers the ability to record the real-time communication with Agora On-Premise Recording SDK and Agora Cloud Recording SDK. The recording files can be stored on the users’ local device or can be stored in a designated cloud storage service chosen by our customers. The local recordings or cloud recordings can be further encrypted through any encryption form of your choosing. Agora does not store any streaming data or user data except for caching for transmission purpose. The cached streaming data of users will be immediately released after the service. Data centers hosting Agora services are maintained by certified and industry-leading cloud service providers, offering state-of-the-art physical protection for the servers and infrastructure that comprise the Agora environment.
Network security
The production environment, where all our customers data and functional servers reside, are completely separated from our internal organization network including the development and testing environments. This guarantees that all our customers data will stay in the production environment and never be used for development or testing purposes.
Access to the Agora production and non-production network is minimized to the greatest extent. Agora also implements network segmentation in production network based on various factors such as the type of business, the criticality of data, and the potential risks, to secure the sensitive customer data.
DDoS prevention Agora regularly scans our core network nodes in the production environment to check and clear potential security vulnerabilities Anti-DDoS firewalls are configured in each core cloud data center for protection. With more than two hundred distributed data centers around the world, Agora can guarantee you with sufficient capabilities and resources to minimize the impact of DDoS attacks and ensure high-availability of real-time video and audio anywhere around the globe.
Monitoring, logging and analysis Agora continuously monitors and analyzes log events to gain a comprehensive view of the security state of our production environment. The logging covers both successful and unsuccessful security events, with an emphasis on the event data of critical infrastructure.
To provide customers with better visibility and security insights, Agora Analytics is made available to consumers as a tracking and analysis tool. This tool enables customers to efficiently locate quality issues and identify root causes for a better end user experience.
The tool contains the Real-Time Alarm function, which enables you to monitor call quality and informs you in real time when the user’s communication experience is below expectation. With Real-Time Alarm, you can undertake the following actions in real time:
- Monitor users who are having poor communication experience.
- Identify abnormalities, analyze quality factor, and locate the source of an abnormal issue.
Network geo-fencing Agora has embedded Network Geo-Fencing in Real-Time Voice, Video and Messaging SDKs to ensure your data is secured from the rising concerns in network security and privacy breaches. Agora Network Geo-Fencing establishes a virtual boundary within the SD-RTNTM and you have the choice to restricted your network traffic in one or more designated region(s).
Network redundancy Agora has more than 200 data centers POPs (Points of Presence) across the world, covering the United States, Europe, China, Japan, India and Asia Pacific and other areas. The POPs in the SD-TRN network adopt the full mesh topology with superior routing capabilities. This is to ensure that the network services are not interrupted due to a single point of failure. The POPs build fault tolerance and disaster recovery capability of Agora service across the regions.
POPs also measure the performance of every possible path through the global network to find the “optimized” paths to ensure high data packet delivery success rate within the smallest time window.
Expert guidance
Agora provides expert guidance to our customers on how to leverage our security features and embed best practices into every layer of your application.
Security compliance audit
Agora is continuously monitoring, auditing, and improving the design and operating effectiveness of our security controls. These activities are regularly performed by both third-party credentialed assessors and Agora’s internal risk and compliance team. Audit results are shared with senior management and all findings are tracked to resolution in a timely manner.
Penetration testing
In addition to third-party security compliance audits, Agora engages Trustwave SpiderLabs to conduct network penetration tests at least annually. Results of the penetration testing are shared with senior management and are triaged, prioritized and remediated in time. Agora customers may receive executive summaries of these activities by requesting them from their account managers.
Data security and user privacy are the top priorities of Agora. Agora is committed to building a professional RTE PaaS with Compliance, Safety, Security, and Trust. It is a critical responsibility for Agora to help ensure the confidentiality, integrity, and availability of systems and data, and Agora continues to work hard to maintain that trust. If you have any questions or concerns, please contact our security team or account managers.
ISO certificates
Security and compliance are the basic requirement for real-time interaction. Agora complies with the compliance requirements of different countries and industries to create safe and reliable cloud services.
The ISO certification of Agora has passed the supervision and accreditation of three different certification organizations: IFA CNAS (China National Accreditation Service for Conformity Assessment), UKAS (United Kingdom Accreditation Service), and DNV (Det Norske Veritas). Agora builds cloud service technology worldwide in accordance with internationally recognized standards to ensure the information security of global customers.
ISO certifications of Agora
ISO/IEC 27001: 2013
ISO/IEC 27001: 2013 is the most authoritative, widely accepted and applied system certification standard in the field of information security. This system covers the information security management during the global operation and maintenance of Agora's cloud platform for real-time engagement.
Click to download the certificates:
ISO/IEC 27017: 2015
ISO/IEC 27017: 2015 is a supplementary standard to ISO 27001, which provides information security implementation specifications for cloud service providers.
Click to download the certificate: ISO/IEC 27017:2015
ISO/IEC 27018: 2019
ISO/IEC 27018: 2019 is a supplementary standard to ISO 27001, which provides implementation specifications for the protection of personal information for cloud service providers.
Click to download the certificate: ISO/IEC 27018:2019
ISO/IEC 27701: 2019
ISO/IEC 27701: 2019 is a privacy extension to ISO/IEC 27001 information security management and ISO/IEC 27002 security controls. It is an international standard system of management systems that provides guidance on the protection of personal privacy, including how organizations should manage personal information.
Click to download the certificate: ISO/IEC 27701: 2019
Security best practices
Security and compliance are essential for real-time engagements through technology. In order to provide safe and reliable cloud services, Agora adheres to the compliance requirements of different countries, regions, and industries, in addition to being certified to ISO/IEC 27001. For more information, see ISO certificates.
Agora protection measures against attacks
Agora products and services are designed and built with multiple protection measures against attacks commonly seen in the real-time engagement industry. This article describes some of the security best practices that Agora has adopted, as well as security tools it provides for developers, as follows:
| Protection measures | Applied by default | Recommended use-cases |
|---|---|---|
| Channel seperation | Yes | All real-time use-cases. |
| Token-based authentication | No | All real-time apps in a production environment should use token-based end-user authentication. |
| Encryption | No | Real-time use-cases that require confidentiality. |
| Network geofencing | No | Real-time use-cases where customers wish to restrict access to Agora servers to within a specified region. |
Level 1 - Channels separation
The channels architect is the first built-in layer of protection. Agora creates an independent and isolated channel for each audio, video, or messaging data transmission. All channels are logically separated and only authenticated users from the same App ID can join the same channel.
Level 2 - Token-based authentication
The second layer of protection is on the authentication layer. This is done via using the dynamic token-based authentication. The token is a short-lived access key, which is generated by the app backend and allows users to access the Agora platform after the user is properly validated by the app.
A token is generated with important information such as App ID, user ID (uid), channel name, and expiration date.
Authentication workflow
The app developer can enable token-based authentication (App Certificate) on Agora Console. When enabled, all user’s request to join a channel must be done with a valid token.
Enable token-based authentication
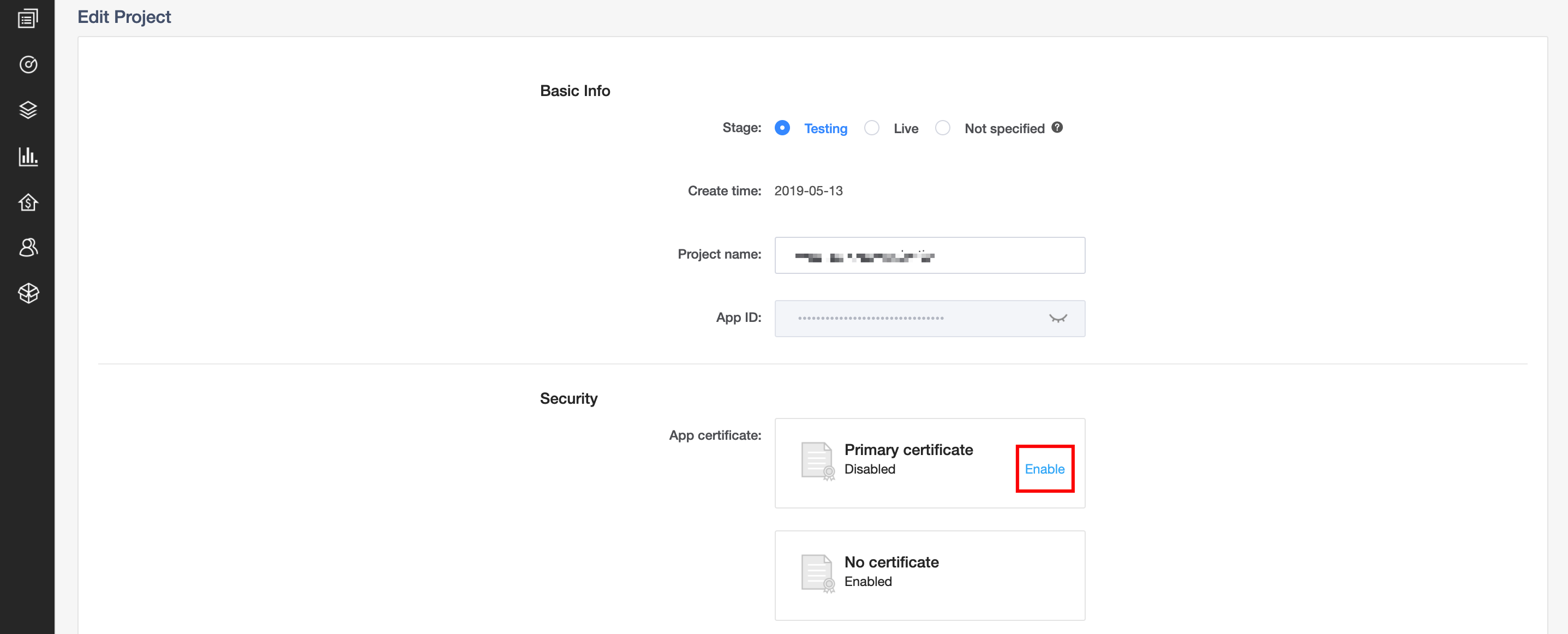
Please note for best security practices, you need to set the token expiration time (24 hours by default). A token has three expiration timestamps:
- Token expiration: How long a token is valid for, that is, how long a user can stay in a channel.
- Privilege expiration:
- Join a channel: How long a token can be used to join a channel.
- Streaming privilege: Whether a user can send audio, video or messaging to the channel, or join as an audience member. This privilege is not enabled by default.
Level 3 - Encryption
The next layer of security in the Agora platform is encrytion. Agora supports transmission encryption and data encryption.
To guarantee data confidentiality during transmission, Agora uses the AUT (Agora Universal Transport) encryption protocol, Agora's proprietary secured transport layer.
Data encryption encrypts all the audio and video streams with a symmetric key and encryption controlled by the app developer. In this level the app provides a symmetric encryption key to the local SDK libraries.
The SDK encrypts all the captured media using the key and the configured encryptions using AES 128/256 (based on configuration). The data is sent encrypted to Agora SD-RTNTM and from there to the other endpoints in the channel. The receiving endpoint will use the key provided by the app layer to decrypt the media streams and send to the renders. With this method, only the application knows the keys. In the Native SDK (iOS, Android, Mac, Windows) the keys are not sent to Agora servers.
Token encryption
When using Other Agora services like Web SDK, Cloud Recording, Content Moderation, Transcoding etc, encryption is done a bit differently and it is not end-to-end. In this case media is still encrypted but the Agora service needs to be aware of the key to be able to connect to the channel and provide service. For example, in Web SDK the User/Browser protection is done via the web-server protection (HTTPS) as well as the WebRTC standard, security practice (encryption, key management etc). More information on WebRTC security can be found here.
The media encryption on Web SDK is done via WebRTC standard but the interoperability to Agora is done using Agora’s encryption engine and the encryption key is passed securely to the Web SDK servers via the APIs. The key is required as the Agora edge server will convert from WebRTC protocols to Agora’s protocol and allow interoperability with Native SDK. Similar situation happens with Cloud Recording, Content Moderation etc., where the Restful APIs are used to securely pass the key for the channel.
Media encryption
Level 4 - Network geofencing
To conform to the laws and regulations of different countries and regions, the Agora Video SDK and the Signaling SDK support network geofencing, which limits the transmission of data to within a specified region.
These SDKs support network geofencing in the following regions: global (default), North America, Europe, Asia (excluding Mainland China), Japan, India, and Mainland China. Once a customer specifies a region using geofencing, no audio, video, or message can access Agora servers outside that region.
Security best practice checklist
Use this list to quickly check what measures you have or have not taken to best protect the security of you app and users:
- Enable token-based authentication on Agora Console.
- Disable No certificate in your project management page. Once it is done your app authenticates users with tokens only.
- Deploy a token server in your backend services.
- Protect the token server and only allow the app backend server to connect to the token server.
- Set the token expiration date to a reasonable time. See the description of the
expireTime parameterin API Reference. - If needed, contact support@agora.io to enable token privilege and set token per role.
- For additional security if needed work with the Agora SA team to customize the token server and modify the token join privilege to a low time, like 5 min. This is more advance and recommended after app development is completed.
- Channel encryption key management – generate a random key (secret) per channel at the time of creating the channel, do not reuse encryption keys.
- Pass the channel encryption key (secret) securely outside of Agora engine to authenticated endpoints that are allowed to join the channel.
- For additional security, you can also do the following:
- Set the “Agora channel name” to a one-time random string managed by your app.
- Set the Agora
uidto a one-time numeric id that is mapped to the user on the app level. Do not use the users' real ID on your app as the Agorauid.
Agora bug bounty program
Agora is always looking to better protect our system and customers. Therefore, we invite security researchers to report any bugs or vulnerabilities they discover to us.
Once we receive notice of a bug or vulnerability, Agora customer service and security teams will respond quickly to address the issue.
In addition to our gratitude, those who report a vulnerability may be eligible for a monetary “bounty” based on the risk associated with the vulnerability and the importance of the affected system.
System importance classifications
The following table shows system importance classifications (in descending order), along with some example Agora assets:
System importance classifications
| Classification | Asset Examples |
|---|---|
| Core system | SD-RTN™, the mail system, and official websites such as www.agora.io, sso.agora.io, and api.agora.io |
| General system | Forums and the Developer Portal (docs.agora.io) |
| Fringe system | Test sites |
Vulnerability severity classifications
The following list outlines detailed examples of how various vulnerabilities would be classified:
Severity classification examples
Critical
- Unauthorized system privileges Examples include command injection (execution), code injection (execution), web shell execution, SQL injection, and buffer overflow that gains system privileges on the core system.
- Direct denial of service Examples include actions that make service unavailable, reduce service quality, and so on.
- Sensitive information leakage Examples include SQL injection of the core database (identity, order), unauthorized disclosure of sensitive information relating to a user, product order, or payment method, and so on.
- Serious logic design flaws and process defects Examples include the ability to send batches of fraudulent messages, account consumption through a business interface, and large-scale modification of account passwords, and so on.
High
- Sensitive information leakage Examples include unauthorized disclosure of sensitive information relating to a source code, hardcoded passwords, and so on.
- Unauthorized access to sensitive information Examples include bypassing authentication or backend password, leading to unauthorized access to sensitive intranet information.
- Unauthorized sensitive operations Examples include manipulating important information without authorization, such as orders, major business configurations, and so on.
Medium
- Vulnerabilities that require interaction and affect users Examples include stored XSS (cross-site scripting).
- General unauthorized operations Examples include incorrect direct object references, unauthorized access to orders, unauthorized access to user information, and so on.
- General information leakage Examples include client-side stored plaintext passwords, system path traversal, and so on.
- General logic design flaws and process defects
Low
- Local denial of service vulnerabilities, CSRF (cross-site request forgery), reflected-XSS, and so on.
- Minor information leakage, such as path information, SVN information, exception information, the local SQL injection of a client-side application (limited to database name, field name, log print), and so on.
- Vulnerabilities that are difficult to exploit but still have security implications, such as plaintext transmission of passwords.
Info
-
Exposure of software banners, internal IP addresses, some public email addresses or phone numbers, and so on.
-
Using outdated versions of a system, supporting outdated version of an encryption protocol, such as SSL (secure-sockets layer) or tls (transport-layer security) 1.0, supporting low-strength encryption algorithms, and so on.
Bug Bounties
Please report any potential risks of Agora services that you may notice to security@agora.io . Any bounties awarded will conform roughly to the following ranges (based on the severity and system location of the bug or vulnerability, payable in $US):
- Critical: $300 to $5000
- High: $200 to $2000
- Medium: $150
- Low: $50
- Info: $0
Note: Agora reserves the sole right to determine any reward amount given.



